🔐 Enhancing Security with OpenID Connect
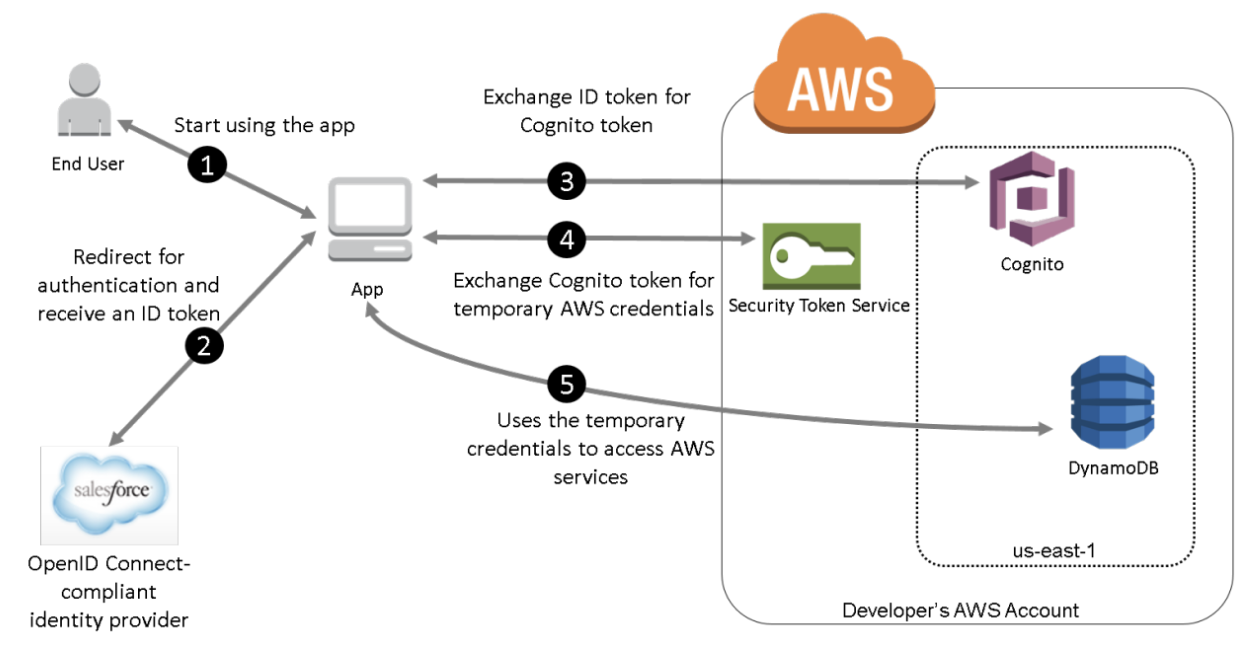
Security is a top priority when managing cloud environments, and one way to enhance it is through identity management solutions like OpenID Connect (OIDC). In a recent project, I explored how to create and configure an OIDC identity provider (IdP) with AWS Identity and Access Management (IAM), allowing secure, short-term access to AWS resources using JSON Web Tokens (JWTs). This project helped me deepen my understanding of authentication and authorization protocols while applying them in a real-world context. 🌐
Why OpenID Connect? 🛡️
OpenID Connect (OIDC) is a standard authentication protocol that enables secure authentication between systems without directly managing user credentials. Integrating OIDC with AWS means external applications can authenticate users and request temporary AWS credentials, making it an excellent choice for federated identities, like mobile and web applications. 📲
Project Overview: Implementing OIDC in AWS 🚀
- Setting Up the OIDC Identity Provider in IAM: The first step involved creating an OIDC IdP in IAM, allowing a third-party application to authenticate users and request AWS credentials. By configuring the provider URL and audience (sts.amazonaws.com), I linked the external IdP to AWS, ensuring that trusted requests could access AWS resources. ✅
- Creating an IAM Role for OIDC: Next, I set up an IAM role specifically for the OIDC IdP. This role doesn’t have long-term credentials but instead allows trusted users to assume the role temporarily. I assigned policies to grant read-only access to Amazon EC2, ensuring the external application could interact with AWS securely but with limited permissions. 📋
- Testing with JSON Web Tokens (JWTs): Once the IAM role was in place, I used a simulated web application to generate a JWT. The JWT contained vital information like the audience (sts.amazonaws.com) and the issuer, confirming that the token originated from the trusted IdP. By passing the JWT to AWS Security Token Service (STS), the application received short-term credentials, which were then used to describe EC2 instances. 🖥️
Overcoming Challenges 🛠️
Configuring the OIDC IdP and ensuring that the trust relationship between the IdP and AWS was seamless required close attention to detail. Managing the audience and issuer claims in the JWT was crucial, as any mismatches would prevent the token from being accepted. Additionally, verifying that the temporary credentials worked by calling the DescribeInstances action was a rewarding validation of the setup. 🎉
Key Takeaways 📚
- OIDC Simplifies Identity Management: Using OIDC removes the need to manage user credentials directly, simplifying the process of integrating with third-party identity providers. 🔐
- Short-Term Credentials Enhance Security: IAM roles with temporary security credentials ensure that access is granted only for a limited time, reducing the risk of long-term exposure. ⏳
- JSON Web Tokens (JWTs) Are Powerful Tools: JWTs allow secure communication between systems, and understanding how they work is crucial for modern cloud security architectures. 🛡️
What’s Next? 🔮
This project has strengthened my cloud security skills, and I’m eager to apply OIDC in more complex scenarios, such as integrating with multiple external identity providers and managing cross-account access. As I continue exploring AWS’s vast security capabilities, I’ll share more insights and projects on my website. 🌟
Stay tuned for future updates on techwithnorma.click! If you're working on cloud security yourself, I highly recommend experimenting with OIDC—it’s a robust and scalable solution for securely managing access to cloud resources. 💡